I like IPSec because it was designed to bind 2 networks together from the beginning.
Purpose built engineering. Do one thing, do it well. Its available in IPv4 and IPv6. One of the things that I’ve found difficult to find is documentation for setting up a Juniper SRX for mobile IPSec that works with OS X. After quite a lot of google sifting, and a bit of piecing together, I’ve arrived at a solution which works on 12.1X45, and VPN Tracker 7 . This config supports AES-128, and AES-256, SHA-256, and Diffie-Hellman group 14.
Juniper SRX config
1 set security ike proposal PSK-AES128-SHA256-DH14 authentication-method pre-shared-keys
2 set security ike proposal PSK-AES128-SHA256-DH14 dh-group group14
3 set security ike proposal PSK-AES128-SHA256-DH14 authentication-algorithm sha-256
4 set security ike proposal PSK-AES128-SHA256-DH14 encryption-algorithm aes-128-cbc
5 set security ike proposal PSK-AES128-SHA256-DH14 lifetime-seconds 28800
6 set security ike proposal PSK-AES256-SHA256-DH14 authentication-method pre-shared-keys
7 set security ike proposal PSK-AES256-SHA256-DH14 dh-group group14
8 set security ike proposal PSK-AES256-SHA256-DH14 authentication-algorithm sha-256
9 set security ike proposal PSK-AES256-SHA256-DH14 encryption-algorithm aes-256-cbc
10 set security ike proposal PSK-AES256-SHA256-DH14 lifetime-seconds 28800
11 set security ike policy IKE-DYN-VPN-POLICY mode aggressive
12 set security ike policy IKE-DYN-VPN-POLICY proposals PSK-AES128-SHA256-DH14
13 set security ike policy IKE-DYN-VPN-POLICY proposals PSK-AES256-SHA256-DH14
14 set security ike policy IKE-DYN-VPN-POLICY pre-shared-key ascii-text PRE_SHARED_KEY
15 set security ike gateway DYN-VPN-LOCAL-GW ike-policy IKE-DYN-VPN-POLICY
16 set security ike gateway DYN-VPN-LOCAL-GW dynamic hostname GROUP_NAME
17 set security ike gateway DYN-VPN-LOCAL-GW dynamic connections-limit 10
18 set security ike gateway DYN-VPN-LOCAL-GW dynamic ike-user-type shared-ike-id
19 set security ike gateway DYN-VPN-LOCAL-GW external-interface ge-0/0/0
20 set security ike gateway DYN-VPN-LOCAL-GW xauth access-profile DYN-VPN-ACCESS-PROFILE
21 set security ipsec proposal ESP-AES128-SHA256 protocol esp
22 set security ipsec proposal ESP-AES128-SHA256 authentication-algorithm hmac-sha256-128
23 set security ipsec proposal ESP-AES128-SHA256 encryption-algorithm aes-128-cbc
24 set security ipsec proposal ESP-AES128-SHA256 lifetime-seconds 28800
25 set security ipsec proposal ESP-AES256-SHA256 protocol esp
26 set security ipsec proposal ESP-AES256-SHA256 authentication-algorithm hmac-sha256-128
27 set security ipsec proposal ESP-AES256-SHA256 encryption-algorithm aes-256-cbc
28 set security ipsec proposal ESP-AES256-SHA256 lifetime-seconds 28800
29 set security ipsec policy IPSEC-DYN-VPN-POLICY perfect-forward-secrecy keys group14
30 set security ipsec policy IPSEC-DYN-VPN-POLICY proposals ESP-AES128-SHA256
31 set security ipsec policy IPSEC-DYN-VPN-POLICY proposals ESP-AES256-SHA256
32 set security ipsec vpn DYN-VPN ike gateway DYN-VPN-LOCAL-GW
33 set security ipsec vpn DYN-VPN ike ipsec-policy IPSEC-DYN-VPN-POLICY
34 set security policies from-zone trust to-zone untrust policy DYN-VPN-policy match source-address any
35 set security policies from-zone trust to-zone untrust policy DYN-VPN-policy match destination-address any
36 set security policies from-zone trust to-zone untrust policy DYN-VPN-policy match application any
37 set security policies from-zone trust to-zone untrust policy DYN-VPN-policy then permit tunnel ipsec-vpn DYN-VPN
38 set security policies from-zone untrust to-zone trust policy DYN-VPN-policy match source-address any
39 set security policies from-zone untrust to-zone trust policy DYN-VPN-policy match destination-address any
40 set security policies from-zone untrust to-zone trust policy DYN-VPN-policy match application any
41 set security policies from-zone untrust to-zone trust policy DYN-VPN-policy then permit tunnel ipsec-vpn DYN-VPN
42 set security policies from-zone untrust to-zone untrust policy DYN-VPN-policy match source-address any
43 set security policies from-zone untrust to-zone untrust policy DYN-VPN-policy match destination-address any
44 set security policies from-zone untrust to-zone untrust policy DYN-VPN-policy match application any
45 set security policies from-zone untrust to-zone untrust policy DYN-VPN-policy then permit
46 set security nat source rule-set untrust-to-untrust from zone untrust
47 set security nat source rule-set untrust-to-untrust to zone untrust
48 set security nat source rule-set untrust-to-untrust rule DYN-VPN-untrust-to-untrust match source-address 192.168.0.0/20
49 set security nat source rule-set untrust-to-untrust rule DYN-VPN-untrust-to-untrust then source-nat interface
50 set security dynamic-vpn access-profile DYN-VPN-ACCESS-PROFILE
51 set security dynamic-vpn clients all remote-protected-resources 0.0.0.0/0
52 set security dynamic-vpn clients all ipsec-vpn DYN-VPN
53 set security dynamic-vpn clients all user USER
54 set security zones security-zone untrust interfaces ge-0/0/0 host-inbound-traffic system-services ping
55 set security zones security-zone untrust interfaces ge-0/0/0 host-inbound-traffic system-services http
56 set security zones security-zone untrust interfaces ge-0/0/0 host-inbound-traffic system-services https
57 set security zones security-zone untrust interfaces ge-0/0/0 host-inbound-traffic system-services ike
58 set access profile DYN-VPN-ACCESS-PROFILE address-assignment pool DYN-VPN-ADDRESS-POOL
59 set access address-assignment pool DYN-VPN-ADDRESS-POOL family inet network 192.168.0.248/29
60 set access address-assignment pool DYN-VPN-ADDRESS-POOL family inet range dvpn-range low 192.168.0.249
61 set access address-assignment pool DYN-VPN-ADDRESS-POOL family inet range dvpn-range high 192.168.0.254
62 set access address-assignment pool DYN-VPN-ADDRESS-POOL family inet xauth-attributes primary-dns 192.168.3.10/32
63 set access firewall-authentication web-authentication default-profile DYN-VPN-ACCESS-PROFILE
64 set access profile DYN-VPN-ACCESS-PROFILE client USER firewall-user password PASSWORD
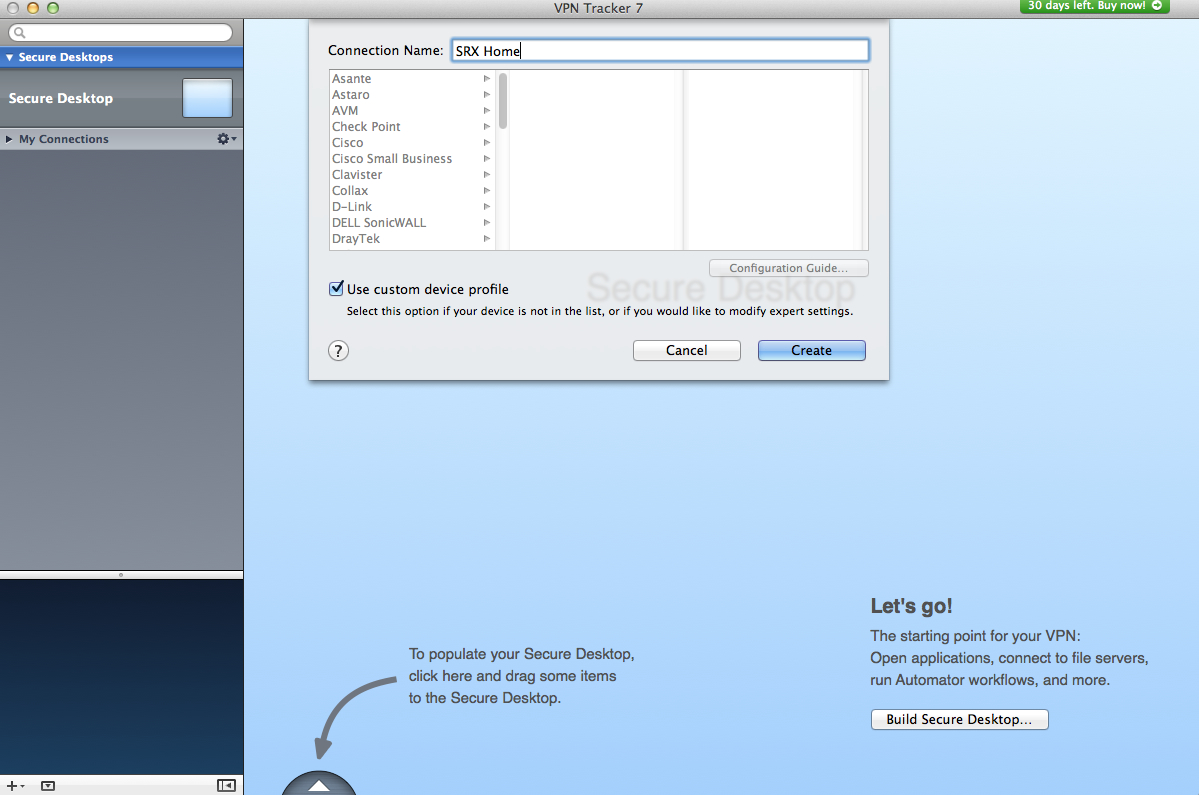
The OS X screenshots
Configuring VPN Tracker - Basic
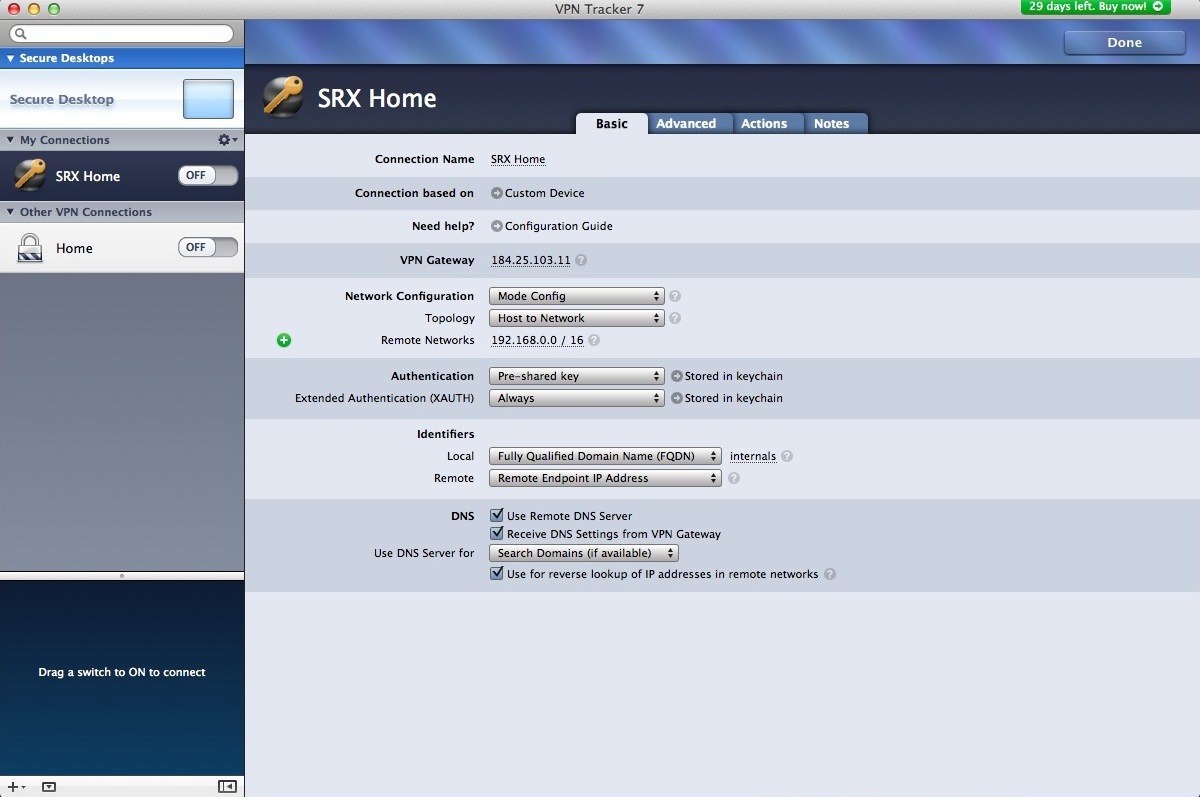
Start with the network configuration. Using Mode config allows you to pass certain options
to the VPN server. The topology is Host to Everywhere. Authentication is pre-shared key.
Next to this, you can actually enter the key. XAUTH is always. Again, you can enter this in
the next field. The Local Identifier is same as the dynamic hostname configured on the srx.
The Remote Identifier is just set to remote IP address. If you need DNS, check the
appropriate boxes.
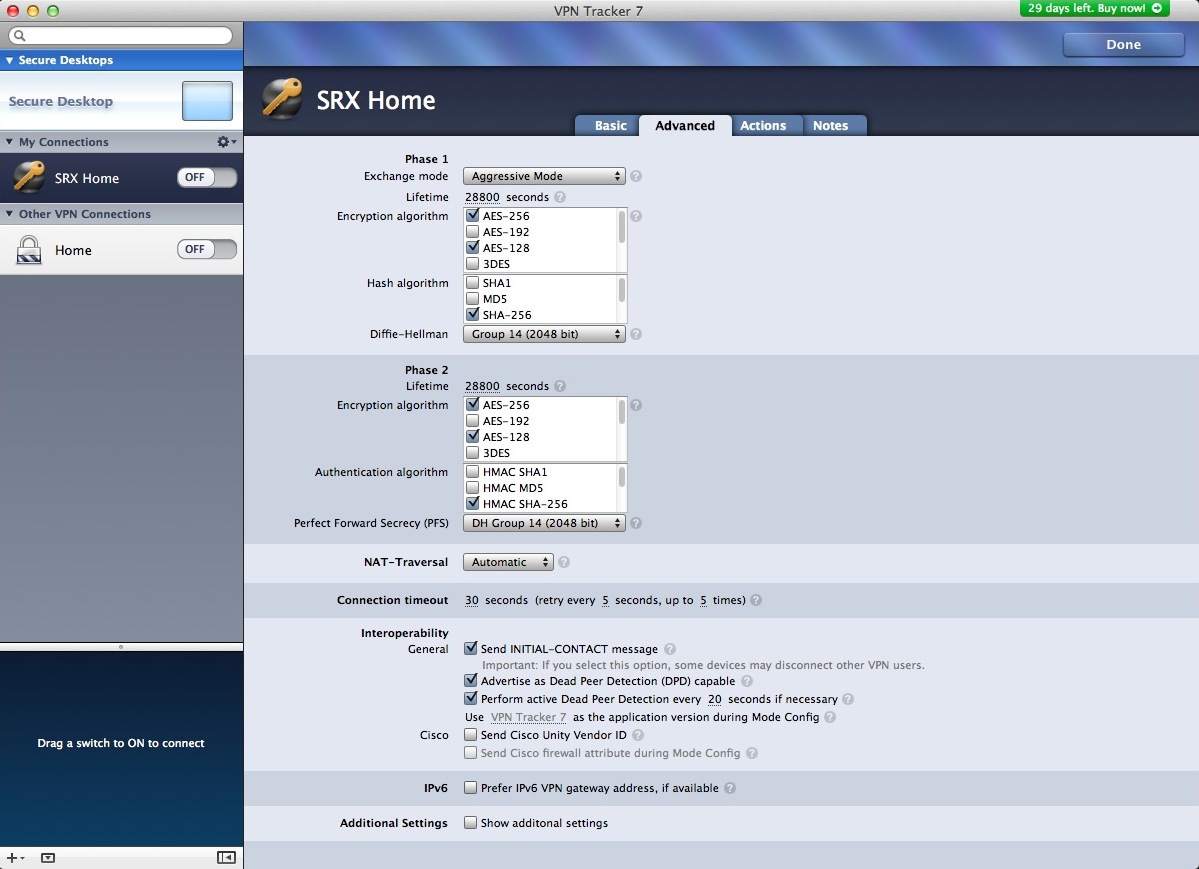
Configuring VPN Tracker - Advanced
PHase 1: Exchange mode should be set to aggressive. Lifetime 28800 (this should match
what is configured on the SRX). Encryption can be one, or both of AES-128, AES-256. Hash
algorithm is SHA-256. Diffie-Hellman group 14 (2048 bit). Phase 2: Repeat the settings for
phase 1, but instead of Diffie-Hellman, its called Perfect Forward Secrecy (PFS). Still
Group 14. Everything below Phase2 can be left as defaults.

Comments